We reduce your Internet attack surface by discovering all your internet facing assets. With the help of a technical attack surface evaluation, you are able to estimate what information an attacker can find on the Internet and how it could be used against your company or national cyber infrastructure. As our own ISP with over 2000 IPv4 scan addresses and unique scan algorithms, our scans lead to advanced and clear scan results.
How it works
”We identify all external IP addresses, network topologies, websites, and vulnerabilities belonging to your enterprise, critical / national cyber infrastructure.
How do we scan
As our own ISP, we maintain more than 2000 different IPv4 and several billion IPv6 addresses. We distribute our scan traffic across multiple scan nodes or IPs on the Internet so that our scans become invisible in the normal noise of the Internet.
We scan the global Internet several times a day. Three billion IPv4 addresses are scanned for various protocols and vulnerabilities.
We offer individual and specific scans. For example, we scan for botnet & C2 infrastructures or other threats on the global Internet.
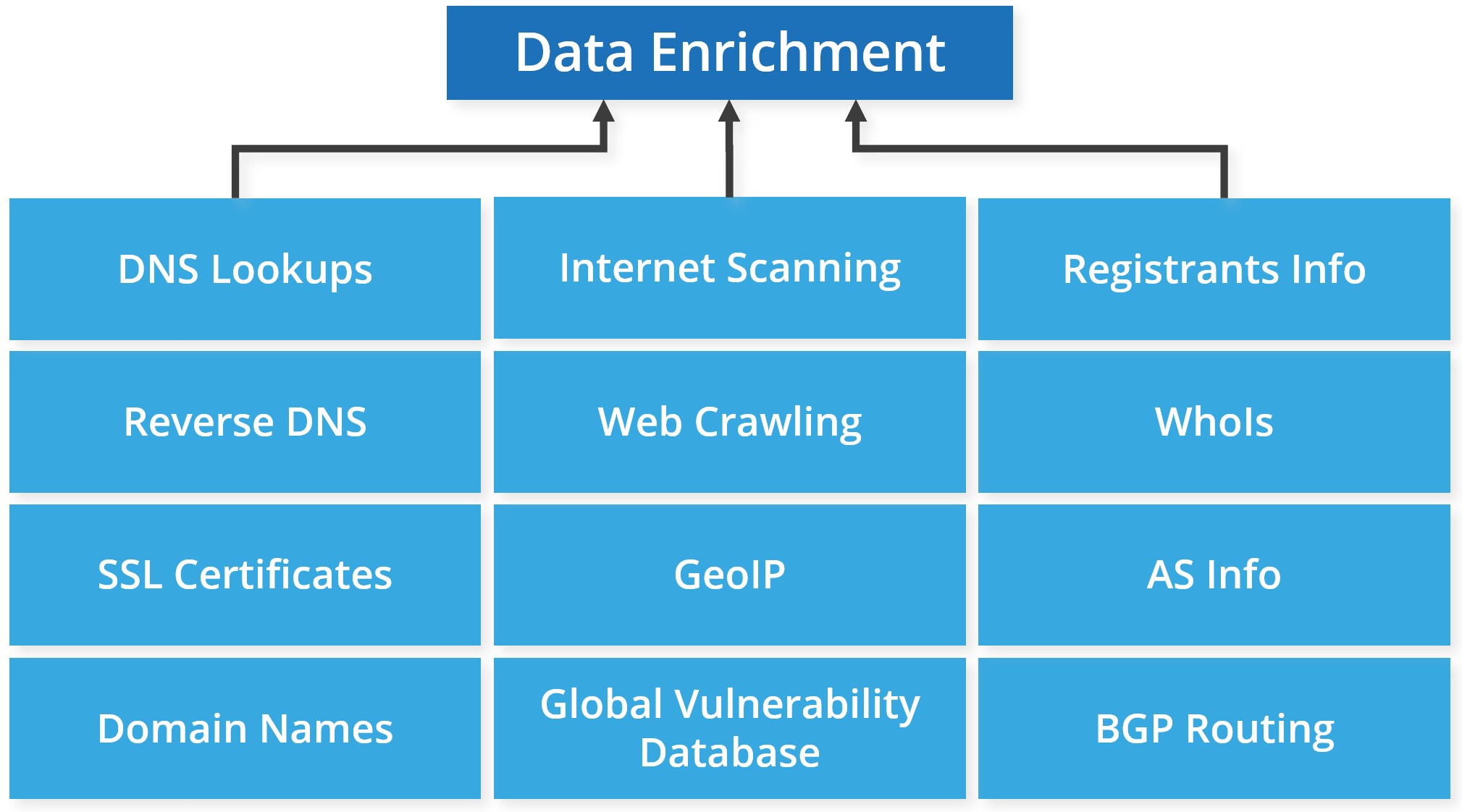
Precise visualization of the cyberspace through data enrichment
The collected scan data is combined with Whois data, IP prefix, Autonomous System (AS) information, certificate information, and geospatial information about the system’s IP.
Combining this information in a Big Data approach provides an exact picture of the cyberspace. This not only allows you to view the distribution of selected system versions of a particular network service or all detected industrial control systems (ICS) on a map, but also to select and aggregate systems by nationality, IP prefix and IP ownership information using dynamic charts. This gives you a quick overview of your own national or enterprise cyber infrastructures.